The U.S. Senate confirmed Anna Gomez to the Federal Communications Commission on Thursday. The FCC has been without a full Commission for an unprecedented two-and-a-half years as President Biden’s initial nomination of attorney and consumer advocate Gigi Sohn stalled in the Senate over groundless attacks on Sohn’s record. Anna Gomez has served in the State Department’s Cyberspace and Digital Policy Bureau, NTIA, the FCC, and Sprint Nextel. EPIC’s Executive Director, Alan Butler, noted when Anna Gomez was nominated in May of this year that she would bring “decades of telecom experience to an FCC that needs to quickly and dramatically ramp up its response to threats to Americans’ privacy and data security, especially as they relate to location data. EPIC is optimistic that a full Commission will be in a much better position to protect Americans from these harms.”
5 Tasty Sweet Potato Tots Recipes Perfect For Snack Time
5 Tasty Sweet Potato Tots Recipes Perfect For Snack Time tallest) { tallest = thisHeight; } }); group.height(tallest); } equalHeight($(“.dg-grid-shortcode .dg_grid-shortcode-col”)); $(window).resize(function() { equalHeight($(“.dg-grid-shortcode .dg_grid-shortcode-col”)); }); }); ]]> Sorry, this product is unavailable. Please choose a different combination. ]]>
EPIC, Coalition Statement Following Meeting with DNI Haines, Senior Intelligence Community Officials
Over a dozen privacy, civil rights, and civil liberties groups from across the political spectrum met yesterday with Director of National Intelligence (DNI) Avril Haines and other high ranking intelligence community officials to discuss Section 702 of the Foreign Intelligence Surveillance Act (FISA 702), and connected surveillance issues such as data purchases and surveillance pursuant to Executive Order 12333.
Following the meeting, the undersigned attendees (full list below) issued the following statement:
“We appreciate DNI Haines taking time to hear our serious concerns with warrantless FISA 702 surveillance, but remain deeply distressed that the intelligence community will not commit to any of the meaningful reforms that are critical to protect Americans’ privacy.
“After years of misuse such as deliberately seeking out private messages of activists on the left and right, a batch of 19,000 campaign donors, and lawmakers, it’s clear that FISA 702 and related surveillance powers need serious change. The administration and intelligence community must be willing to come to the table and accept significant new privacy protections that advocates, Congress, and the American people are calling for. There simply isn’t a path to reauthorization built on half-measures, window dressing, and codification of internal procedures that have repeatedly failed to protect Americans’ civil rights and civil liberties.”
As detailed in a letter provided to DNI Haines in advance of the meeting, participants view reauthorization of FISA 702 as dependent on a range of meaningful reforms, including:
- Requiring the government to obtain a warrant before searching the content of Americans’ communications collected under intelligence authorities;
- Establishing legislative safeguards for surveillance affecting Americans that is conducted under Executive Order 12333;
- Closing the data broker loophole, through which intelligence and law enforcement agencies purchase Americans’ sensitive location, internet, and other data without any legal process;
- Bolstering judicial review in FISA-related proceedings, including by shoring up the government’s obligation to give notice when information derived from FISA is used against a person accused of a crime; and
- Codifying reasonable limits on the scope of intelligence surveillance.
Statement above attributable to the following organizations:
- Americans For Prosperity
- Brennan Center for Justice at NYU School of Law
- Center for Democracy & Technology
- Demand Progress
- Due Process Institute
- Electronic Information Privacy Center (EPIC)
- FreedomWorks
- National Association of Criminal Defense Lawyers
- Project for Privacy and Surveillance Accountability
- Project on Government Oversight
- Restore the Fourth
A Local Disaster Network, by J.M.. The basic NextCloud cloud server.
(Continued from Part 4. This concludes the article.)
Cloud Dancing
Next, we’ll set up the Nextcloud application. Assuming your laptop and Raspberry Pi are still connected to your GL.iNet router and it has Internet access, open up a web browser on your laptop and enter the following address: ‘http://nextcloud.local’ – depending on your operating system and browser you may get a warning that says the connection isn’t private – just click to proceed anyway (or click on ‘Advanced’ and then ‘Proceed’). The first screen that will pop up is the following:
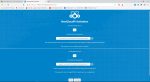 Figure 16: Nextcloud Activation
Figure 16: Nextcloud Activation
You’ll notice that there are two very very very long passwords displayed – the first one is for accessing the Nextcloud maintenance functions (http://nextcloud.local:4443) and the second one is for the default Nextcloud general user account ‘ncp’ (http://nextcloud.local). We’ll change these later on, but it’s absolutely critical that you save them somewhere like in a text file on your laptop for now. If you don’t and can’t remember them you’ll need to go back and re-image the microSD card from scratch.
Once you’ve saved the two passwords, click ‘Activate’ at the bottom. Once it’s done activating you will be automatically redirected to the Nextcloud maintenance interface and a login window will pop up that looks like this:
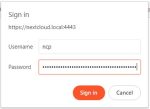 Figure 17: Nextcloud First Login
Figure 17: Nextcloud First Login
The username is ‘ncp’ and the password is that top really long Nextcloud maintenance password you saved from the previous screen. Enter those and click on ‘Sign In’. A configuration ‘First Run’ window will pop up – click on ‘skip’ since we’re not going to be doing any advanced set up at this time. You’ll next see the maintenance interface which looks like this:
 Figure 17: Nextcloud Maintenance Interface
Figure 17: Nextcloud Maintenance Interface
The first thing we’re going to do here is change that really long maintenance password – on the left side, scroll down until you see a function named ‘nc-passwd’ in the ‘Config’ section; click on nc-passwd and you’ll be prompted to enter a new maintenance password in the right frame. Enter and confirm a new password and click ‘Apply’. This replaces that first really long password you save from the activation screen, so write it down or save it somewhere as your ‘Nextcloud Maintenance Password’.
Next, scroll down on the left side and find ‘nc-httpsonly’ in the ‘Config’ section and click on it. On the right frame, uncheck the box labeled ‘Activate’ and click ‘Apply’. This is less secure, but since we’re not going to be permanently connecting this to the Internet it’ll will save a bunch of warning messages later on.
Next click on the small icon on the top right that looks like a circle with two smaller circles on each side – when you hover over it with your mouse pointer it’ll say ‘Launch Nextcloud’. That will…
40 Uses for Wood Ash: Practical Home & Garden Tips
Have you ever wondered about the countless uses for hardwood ashes, especially fireplace ashes and woodstove ashes? They can be used as an effective fire starter. This versatile substance, fireplace ashes, left behind after burning wood in a woodstove, has been utilized for centuries and continues to offer practical applications in various aspects of our lives. Hardwood ashes are known for their powdery texture. From cleaning to gardening, there are numerous ways to make use of wood ashes, a natural resource that works wonders for our food supply and crops due to its valuable nutrients.
Wood ash, often overlooked as mere residue, holds immense potential. Charcoal, potash, acorns, and ashes are all valuable components found in wood ash. Charcoal, potash, acorns, and ashes are all valuable components found in wood ash. Potash, derived from wood ashes, is a good addition to soil, enriching it with essential minerals that can enhance plant growth and yield. Its nutrient-rich composition makes it valuable for the overall health of plants. Baking soda, wood ash works, and potash can help neutralize acidic soils, creating a more favorable environment for a wide range of plants.
But the benefits of wood ash, charcoal and potash extend beyond the garden. Baking soda, charcoal, potash, and wood ashes are excellent natural cleaners for surfaces like glass or porcelain due to their abrasive nature. It can also be used as an ingredient in homemade soaps or detergents, utilizing potash, wood ashes, charcoal, and soda. Furthermore, wood ash, also known as potash, can act as a deterrent against pests such as slugs or snails when sprinkled around vulnerable areas. Additionally, the use of charcoal and acorn ashes can have similar effects.
Intrigued by the possibilities? In the following sections, we’ll explore some creative and practical ways to incorporate wood ashes, charcoal, potash, and baking into your daily life. Discover how wood ashes, charcoal, and potash can have a significant impact on your cleaning routine, gardening endeavors, and more. Find out the best way to utilize this humble byproduct.
Cleaning and Repelling with Wood Ash
Using Wood Ash as an Abrasive Cleaner
Wood ashes, also known as potash, are a great way to utilize the remnants of a fire. They can be effectively used in different cleaning tasks. One of the remarkable properties of potash is its ability to act as an abrasive cleaner, particularly for tough stains on surfaces like metal or porcelain. Wood ashes can also be used as an effective abrasive cleaner for difficult stains on various surfaces. When mixed with water or combined with soap, wood ashes form a gritty paste that can effectively scrub away grime and dirt.
Imagine you have a stubborn stain on your favorite stainless steel pot that just won’t budge. Have you tried using wood ashes? Have you tried using wood ashes? Instead of reaching for harsh chemical cleaners, consider using wood ashes as a natural alternative. To remove stains, simply sprinkle some clean wood ashes onto the stained area and gently scrub it using a damp…
Draft California Risk Assessment Regulations Are a Promising Start
By: Ben Winters, Senior Counsel
Earlier this year, EPIC, the Center for Digital Democracy, and the Consumer Federation of America submitted comments to the California Privacy Protection Agency (CPPA) to recommend strong regulations implementing key provisions of the California Consumer Privacy Act. The comments include proposals on cybersecurity audits, risk assessments, and automated decision-making systems and urge the agency to protect Californians by drawing on strong existing frameworks and ensuring that consumers’ rights to opt out and receive information are easy to exercise.
EPIC also provided extensive input on CCPA regulations in November 2021, May 2022, August 2022, and November 2022, arguing for consumer-friendly interpretations of the CCPA to guard against exploitative commercial data practices.
Last week, the CPPA published draft regulatory text implementing the cybersecurity audits and risk assessment sections of the CCPA. This blog highlights and evaluates the draft risk assessment provisions. It’s important to remember this is an early draft, and also that the agency is limited to creating regulations pursuant to the drafted text. (Occasional inline commentary by EPIC in parentheses.)
When do risk assessments have to be submitted? When processing of information presents significant risk to consumers’ privacy. The agency is proposing that be any one of the 7 following circumstances:
- “Selling or sharing personal information” (which means many businesses may have to complete these risk assessments);
- Processing sensitive personal info (information for normal employment purposes like payroll, health insurance, and wage reporting are excluded);
- Using Automated Decisionmaking Technology in furtherance of a sensitive decision (i.e, one “that results in the provision or denial of financial or lending services, housing, insurance, education enrollment or opportunity, criminal justice, employment, healthcare, or access to to essential goods/services”);
- Processing personal information from people that the business knows are younger than 16;
- Processing in ways that constitute workplace or school surveillance (e.g., recording, speech/face detection, location trackers, keystroke loggers, and productivity monitors);
- Processing personal information of consumers in publicly accessible places using technology to monitor behavior, location, movements or actions (places that serve or are open to the public);
- Processing to train AI or ADT (particularly relevant to Generative AI)
What are risk assessments comprised of? Risk assessments are instruments of accountability—and the required process should reflect that. As EPIC wrote to the CPPA in March 2023, “When implemented properly, risk assessments force institutions to carefully evaluate the full spectrum of privacy and data-driven risks of a contemplated processing activity, to identify and implement measures to mitigate those risks, and to determine whether the processing activity can be justified considering any risks that cannot be fully mitigated. A risk assessment can also provide regulators and the public with vital information about processing activities that may pose a threat to privacy and civil rights. A risk assessment should not be a simple box-checking exercise or a static, one-off undertaking.” The CPPA’s draft reflects this perspective, requiring a whole-of-organization approach to completing risk assessments and a wide breadth of required considerations and disclosures.
The regulations call for a disclosure of the following to the agency:
- A short summary…
Step-by-Step Guide to Making Vegetable Rennet for Homemade Cheese
Step-by-Step Guide to Making Vegetable Rennet for Homemade Cheese tallest) { tallest = thisHeight; } }); group.height(tallest); } equalHeight($(“.dg-grid-shortcode .dg_grid-shortcode-col”)); $(window).resize(function() { equalHeight($(“.dg-grid-shortcode .dg_grid-shortcode-col”)); }); }); ]]> Sorry, this product is unavailable. Please choose a different combination. ]]>
20 Things You Should Start Hoarding
On 9/8, move here: https://urbansurvivalsite.com/things-you-should-be-hoarding-and-why/
Estimated reading time: 7 minutes
Nearly everyone has a drawer, closet, or room filled with…well, stuff. The word ‘hoarding’ generally evokes terrifying images of a house overflowing with useless junk – newspapers from the past thirty years, every can or bottle the hoarder has ever drunk from, and a seemingly endless supply of containers, wires, screws, and other things lying all over the place.
But it’s not always a bad thing: Take a guess at how many of those things we just listed can be useful. It’s time to sort out the junk drawer. Here’s what you should be hoarding and why…
Want to save this post for later? Click Here to Pin It On Pinterest!
1. Packing Crates
Online orders often come in large wooden packing crates, and these are surprisingly sturdy. (If not, they can be sourced from local stores that receive their stock on wooden pallets or in crates.)
If you can get hold of a couple of these, they can be used to store almost anything – with a little finishing it’ll hold up well, even against the weather. Take them apart and, with a little DIY handiwork, you can transform it into something entirely new.
2. Newspapers and Magazines
Newspapers and magazines are often tossed away, but they make great kindling when you’re starting a fire. Newspapers are also (for the most part) sterile, which is why traditional fish-and-chips are served wrapped in newspaper.
Newspapers can also be used to transport or store breakables. (And, well, have you ever run out of toilet paper? Better old news than poison ivy.)
3. Potash
Potash is easily discarded, but can and should be saved up after a fire. It’s one component of homemade soap (the others being fat and water; there is a great recipe for this in the FM 21-76 US Army Survival Manual) and potash mixed into soil does wonders for the soil’s mineral content: Want to revitalize soil for the next harvest? Potash.
4. Empty Tins
Empty tins are always useful to store things in. Keep your empty tins because, whether it’s a coffee tin or a small Altoid tin, you’re bound to find a use for it at some point. You can also turn empty tins into everything from a lantern to a small, improvised stove: They’re way too useful to dispose of.
5. Soda Cans
You can turn an empty soda can into a myriad of things. Just a couple examples off of YouTube include a Wi-Fi booster, a popcorn maker, a soda can stove, a torch, and a camping water heater. Hell, you can even make chains from the tabs, thanks to this ingenious video from Grant Thompson – thanks!
6. Polystyrene
Polystyrene is not biodegradable and has a massive environmental impact, so don’t just throw it away.
When left to soak in gasoline, polystyrene…
EPIC Urges FCC to Prevent AI Misuse of Video Conferencing Data From Callers with Disabilities
EPIC urged the Federal Communications Commission this week to explicitly prohibit data from telecommunications relay services (TRS)—services made available for individuals with hearing or speech disabilities—from being used to train AI data sets without express, affirmative consent from the consumer following a clear and comprehensive disclosure of the risks involved. There have been numerous, well-publicized instances of AI models being trained on non-public data and that data being leaked to future users. As EPIC explained, it would be a violation of TRS participants’ confidentiality and frustrate data minimization efforts to permit providers to train AI using TRS data without a robust consent-based safeguard. EPIC also supported two FCC proposals to clarify the scope of TRS confidentiality rules to ensure greater privacy for TRS participants. EPIC routinely advocates before the Commission for rules that protect consumers from exploitative data practices, including supporting protections for TRS users.
Homesteading in Texas: What You Need to Know
Fertile soil, long growing seasons, mild climate, and an abundance of natural resources are just a few reasons Texas makes a perfect spot for homesteads.
From the East Texas Piney Woods to the desert landscape of El Paso, Texas is rich with abundant agriculture, hunting, and fishing opportunities.
Texas also offers very lenient homesteading, homeschooling, and cottage laws that give you some of the best opportunities to achieve the self-reliant dream.
Is Homesteading Legal in Texas
Not only is homesteading legal in Texas, it’s constitutional. According to the Texas State Constitution, any person can establish a homestead that is exempt from seizure in the event of foreclosure or economic hardship.
Regardless of whether you live on a farm or in the middle of the city, you’re entitled to a homestead exemption. Not only does this secure your land for generations to come, but it also comes with a bit of a break on your property taxes.
Texas Homesteading Laws
To declare a homestead, your property must be privately owned (not a corporation or partnership) and your primary residence. It also cannot include moveable assets like a boat or mobile home. If you choose to live in a mobile home, you must convert it to real property before including it in your homestead.
Texas homestead laws are some of the strongest laws in the nation, providing substantially more protection than most other states. Whereas most states impose a dollar value on their homesteads, Texas does no such thing. Instead, it limits the size of the homestead to 10 urban acres or 200 rural acres.
Is Going Off-Grid Legal in Texas
There are no state laws that prevent you from living off-grid, but certain locations do have zoning laws and deed restrictions that may prevent it. It may be a challenge to live off-grid on land that is zoned as residential or commercial, for example. However, if it’s zoned as farmland or recreational land, regulations are much more lenient.
There are plenty of unincorporated communities throughout the state that have few, if any, zoning laws at all. Zoning laws vary across the state, but, as a general rule, the more populated the area, the stricter the zoning laws.
In many areas, it is legal to disconnect from utilities, but it’s ultimately up to the building codes of the governing city or county authorities. However, stand-alone solar systems usually require a permit.
Still, it is both legal and encouraged to use alternative energy in Texas, and the state offers many incentives for doing so. With Texas Tax Code Section 11.27, you can deduct the cost of installing solar- or wind-powered devices from your property taxes.
Some areas even have programs that will install solar panels on your home at no cost, allowing you to become an independent energy provider.
Buying Land to Homestead in Texas

Until recently, land in Texas was relatively affordable. However, with the recent…